The true test of security lies in the strength of its weakest link. No matter how robust other security measures are, if one part is vulnerable, the entire cybersecurity ecosystem is at risk.
In today’s rapidly changing cybersecurity world, there is hardly any room for error. It’s essential for businesses to gain clarity in understanding ransomware—its mode of operation, how to prevent it, and how to effectively safeguard operations from it. Uncover five facts about ransomware and have the upper hand in managing emerging threats and proactively protecting your systems and data.

Fact #1 Go beyond minimising risk at the initial intrusion point
Security strategies tend to rely on penetration testing and phishing training for employees to keep the business safe. These are undoubtedly crucial factors in a security plan, but it leaves out the next phase of damage control—when an attacker finds an avenue to enter. The next steps after a breach are just as important, if not more so.
Fact #2 A basic oversight? A threat overnight
In the cybersecurity world, the assumption that all cyberattacks are inherently advanced and complex is frequently met with scepticism, mainly due to the lack of concrete evidence to support such claims. However, since most companies operate with inadequate cybersecurity frameworks, cybercriminals do not necessarily face significant hurdles in penetrating their systems.
Without a formidable solution to fill the gaps in cybersecurity coverage or talents with distinct skill sets, IT systems and networks could fail to maintain cybersecurity best practices, leaving them open to vulnerabilities.
Fact #3 Steps for proactive maintenance of digital security
With the increasing reliance on digital systems and networks, it becomes essential for organisations to protect their data from threat actors. However, many companies are unable to fund cybersecurity efforts adequately due to limited budgets because funding is concentrated on systems and solutions instead. This can leave them vulnerable to attackers that seek out exploitable weaknesses using techniques like ransomware, advanced malware, and phishing attacks.
Fact #4 The unshakable silence about ransomware attacks
We only hear about ransomware attacks through headlines. The most telling details of the attack itself are relatively unknown. This leaves out crucial information other businesses could learn and improve from, like the methods and mode of exploits used. It is, therefore, difficult to understand and decipher the exact plan of attack and the latest techniques applied.
Fact #5: Zero Trust—the only trust you can rely on
The Zero Trust mindset in cybersecurity assumes that no one can be trusted and everything must be verified before granting access. This offers many benefits, including the ability to give the right access and tools to the right people, limiting lateral movement in the event of a compromise, better visibility into network activity, and enhanced compliance.
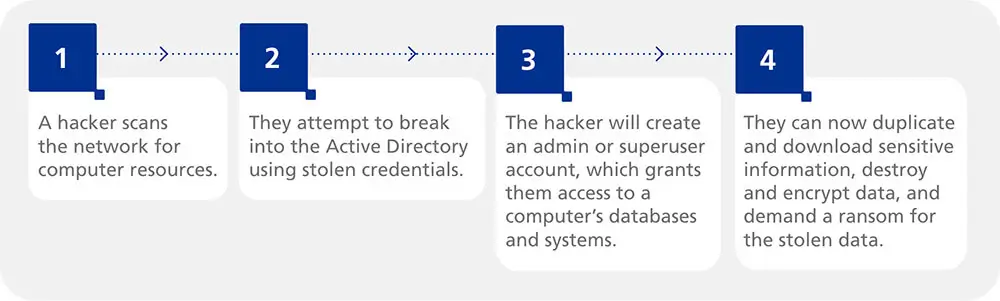
The Four Steps of a Ransomware Attack
It is vital to adopt a culture of ‘security by design’ in your cybersecurity framework to limit the risk of your network being infiltrated. This is because the culture takes a proactive, pragmatic, and strategic approach in dealing with risk and security, which improves your overall posture in facing evolving digital threats.
Ready to Deploy Ricoh’s Cybersecurity Solutions?
With the right approach, mindset, and tools, you will be able to manage risk better. In this ever-changing digital landscape, it is necessary to have the right cybersecurity solution provider by your side. Ricoh’s cybersecurity solutions, combined with our curated partnership with leading cybersecurity specialists, can give you the confidence to do business while we help protect your organisation from threats.
Our key benefits include:
- Ransomware mitigation, which reduces the risk of reputation damage and business showdown
- Helping operations continue despite an attack
- Reducing visibility to ransomware attackers
- Enhancing your IT security posture
- Adding rigour to your IT compliance practice
- Round the clock expert cybersecurity support.


Let’s connect
Talk to a Ricoh expert. Discover how we can help you strengthen your end-to-end cybersecurity measures to ensure compliance and protect your business digitally.
Recommended resources for you

The Cloud Computing Advantage
Why do you need to embrace the future of cloud computing? This ebook highlights the advantages of fully virtualised environments in transforming your business.

Elevate Your Business Potential With Network Cloud Solutions
Learn how to harness the power of network cloud solutions to achieve new heights of efficiency, scalability, and security in the digital age.

Bridging Creativity and Productivity in the Modern Workplace
Strike a balance between creativity and productivity in your organisation with innovative solutions that empower effective collaboration in a modern workplace.